Which of the Following Is Used as a Cryptographic Primitive
I wouldnt consider SHA3 to be a primitive but hash function is. Define cryptographic primitives a.
What Are Some Good Uses Of Cryptography Quora
Comments about specific definitions should be sent to the authors of the linked Source publication.
. Cryptographic primitives are one of the building blocks of every crypto system eg TLS SSL SSH etc. Begingroup A primitive is anything sufficiently generic but the term should refer to the abstract syntaxsecurity definitions not specific constructions. The following manuscript presents a novel approach for the classification of cryptographic primitives in compiled binary executables using deep learning.
This crypto primitive has far reaching implications on secure. BCRYPTPRIMITIVESDLL is a dynamicallylinked library providing cryptographic primitive services. These building blocks are a part of a cryptosystem which is a suite of cryptographic algorithms needed to implement a particular.
Use of a Cryptographic Primitive with a Risky Implementation. Step 1 of 4. Primitives can be used to build other primitives.
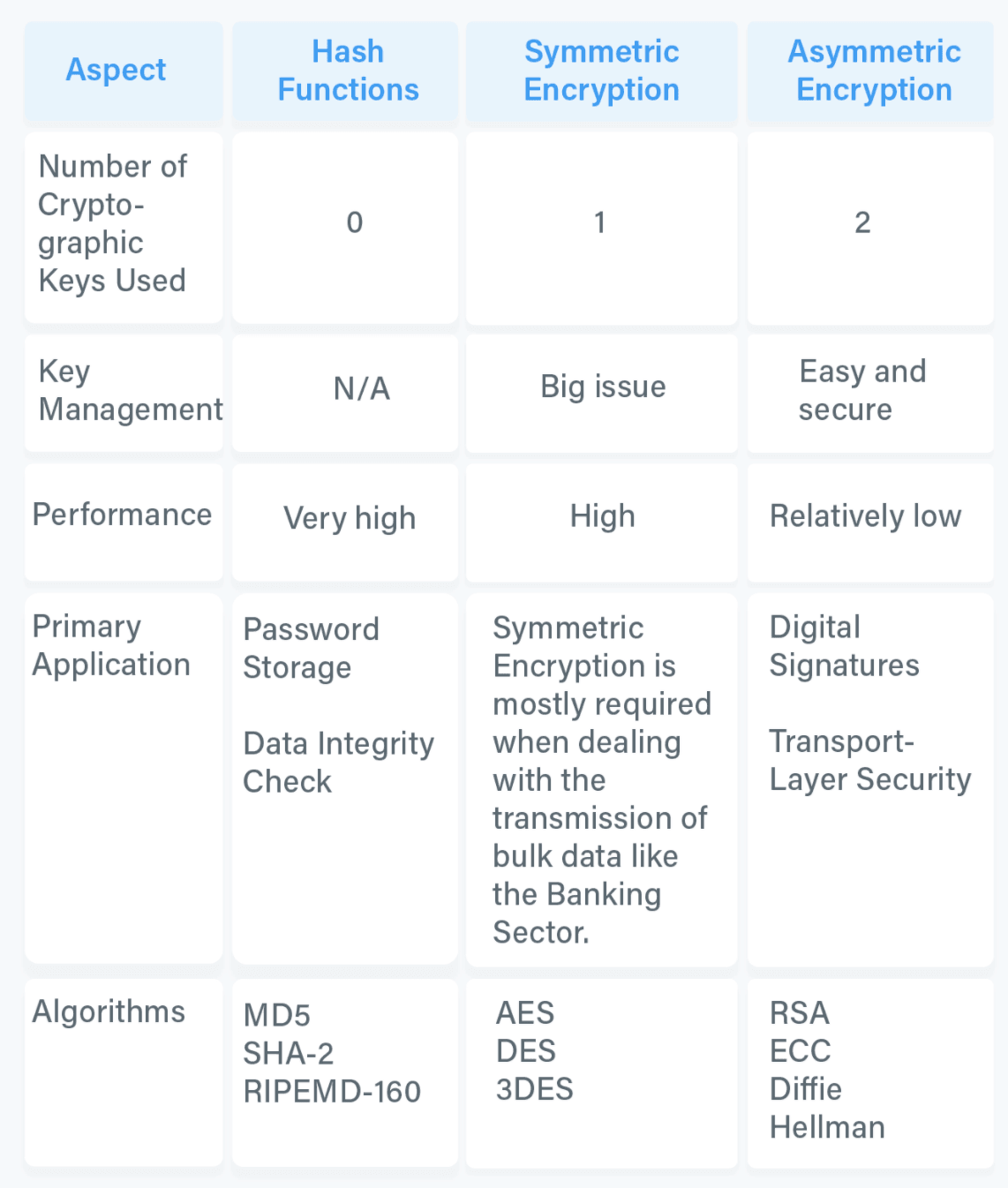
Cryptographic Hash Function or One-Way Hash Function -- compute a reduced Hash value for a message. Q3 What is the most appropriate cryptographic primitive to use if an individual wants to ensure confidentiality of the files stored on her hard drive. Digital Signature - confirm the author of a Message.
Hashing functions is used to verify message integrity and it is combined with any of cryptographic algorithms to build cryptographic primitives. Cryptographically secure pseudorandom number generator. Hash function returns hash values.
Multi-purpose applications that may use cryptography in. Choosing the best primitive available for use in a protocol usually provides the best available security. Deep Learning Based Cryptographic Primitive Classification.
Its used by cryptographic designers as their most basic building blocks. Hashing function alone cannot be used as cryptographic primitive. From the senders point of.
A compression function is a primitive that can be used to build a CRHF primitive which can be. Aw renders the cryptographic primitive unrealistic. Crypto system designers not being in a position to definitively prove their security must take the primitives they use as secure.
For example suppose that for a specific cryptographic primitive such as an encryption routine the consensus is that the primitive can only be broken after trying out N different inputs where the larger the value of N the stronger the cryptography. Asymmetric public key algorithms that support encryption such as RSA. Cryptographic Primitives March 26 2007 Therefore p and q are the roots of the equation x2 nϕn1xn 0 Computing roots.
14 rows For both the verification the existing cryptographic primitives are used. However the notion of primitive can vary depending on point of view. View Test Prep - chap567 from CIS 3630 at University Of Central Missouri.
2 Di erent con dentiality levels Con dentiality is a fundamental information security objective which is a service used to keep the content of information from all but those authorized to have it. Signature algorithms such as DSA and ECDSA. A low-level cryptographic algorithm used as a basic building block for higher-level cryptographic algorithms.
Strated that cryptographic primitive. Behavior property technology language and resource. 13 Validated Platforms The Cryptographic Primitives Library component listed in Section 11 was validated using the following machine configurations.
For example elliptic. If Eve can compute eth roots modulo n then she can compute the plaintext. Cryptographic primitives are defined to accomplish one very specific task in a precisely defined and mathematically reliable fashion.
Algorithms used for hashing such as SHA1 and SHA2. This class can also be used with RSA. Algorithms used for symmetric encryption such as AES 3DES and RC4.
Next Generation CNG defines the following functions that are used for performing cryptographic operations. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions. Pankaj GuptaCrypto Digital Currency MoneyJune 6 2021June 6 202114 Minutes.
Cryptographic protocols and systems depend on cryptographic primitives and associated algorithms as their basic building blocks. Also even more obviously the security of RSA also depends upon the difficulty of computing eth roots modulo n. This post describes a simple but foundational new cryptographic primitive called LimitedUseKey or LUK introduced in Android 12 aka Android S to be released later this year.
The following manuscript presents a novel approach. For NIST publications an. A cryptographic primitive is a low-level algorithm used to build cryptographic protocols for a security system.
Some common examples of primitives are digital signatures one-way hash functions ciphers and public key cryptography.

Ldapwiki Cryptographic Primitive
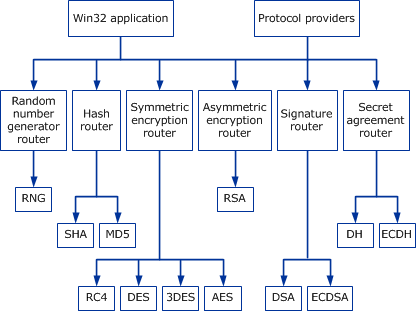
Cryptographic Primitives Win32 Apps Microsoft Docs

Cissp Practice Questions 20220105 By Wentz Wu

Cryptographic Primitive An Overview Sciencedirect Topics
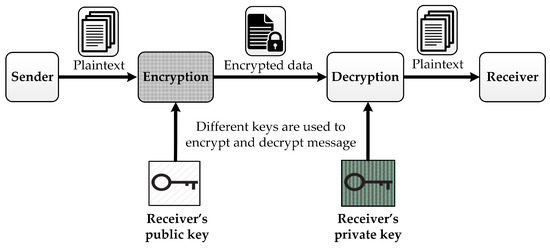
Electronics Free Full Text An Analysis Of Hardware Design Of Mlwe Based Public Key Encryption And Key Establishment Algorithms Html

2 Taxonomy Of Cryptographic Primitives Download Scientific Diagram

Glossary Of Security Terms Cryptographic Hash Function Cryptography Certificate Authority Session Hijacking

Cryptography And Cryptocurrencies Putting The Crypto In Currency
Cryptography And Cryptocurrencies Putting The Crypto Into Currency

Cryptographic Primitives Foundations Of Blockchain Book

Cryptographic Operation An Overview Sciencedirect Topics
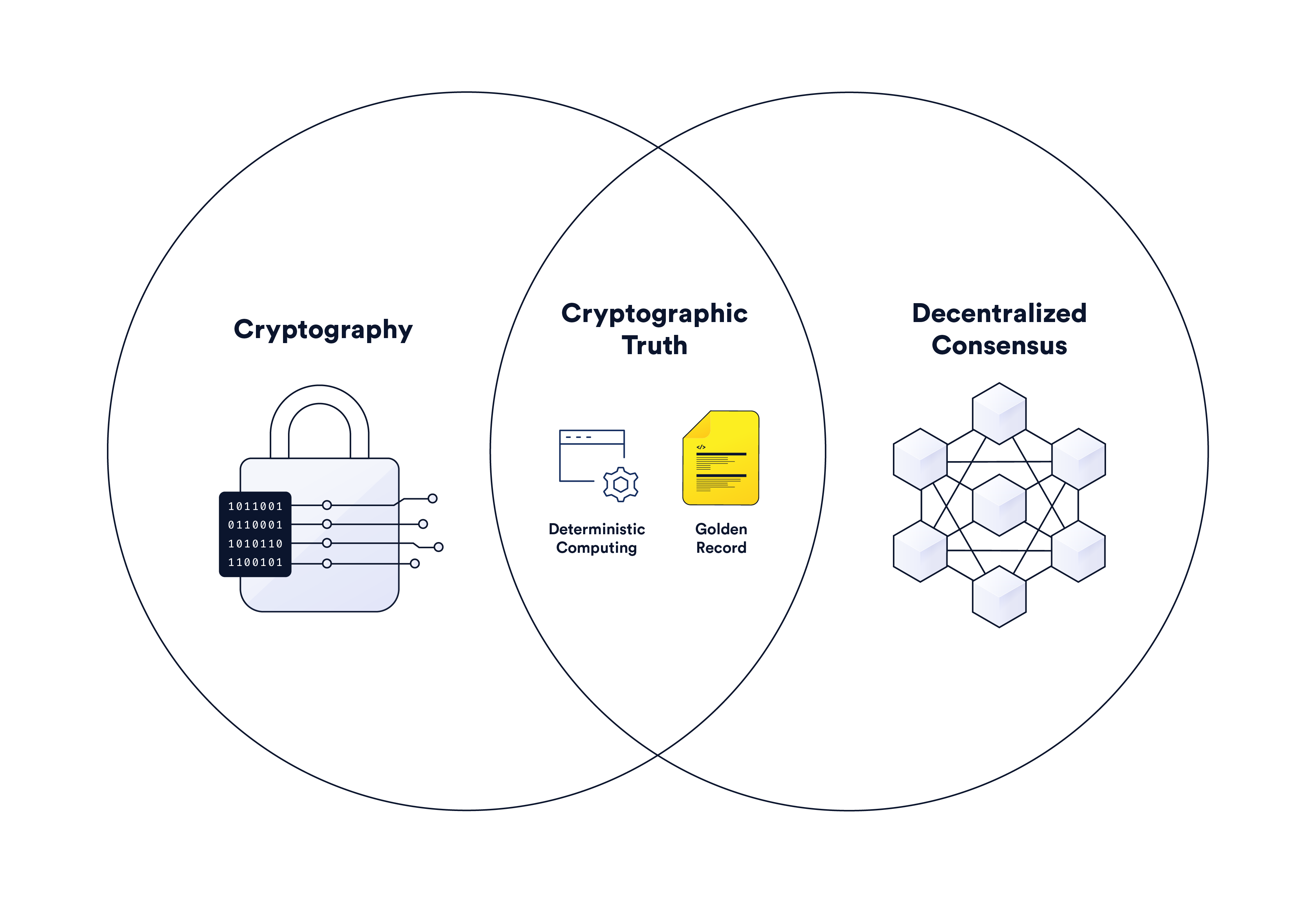
Cryptographic Truth In Record Keeping Backend Computing Chainlink

Lightweight Cryptographic Primitives Download Scientific Diagram

Determination Of Factors That Affect The Design Of Cryptographic Algorithms By A Cybernetic Meta Model Validated With Q Analysis

Analysis Of Attribute Based Cryptographic Techniques And Their Application To Protect Cloud Services Belguith Transactions On Emerging Telecommunications Technologies Wiley Online Library
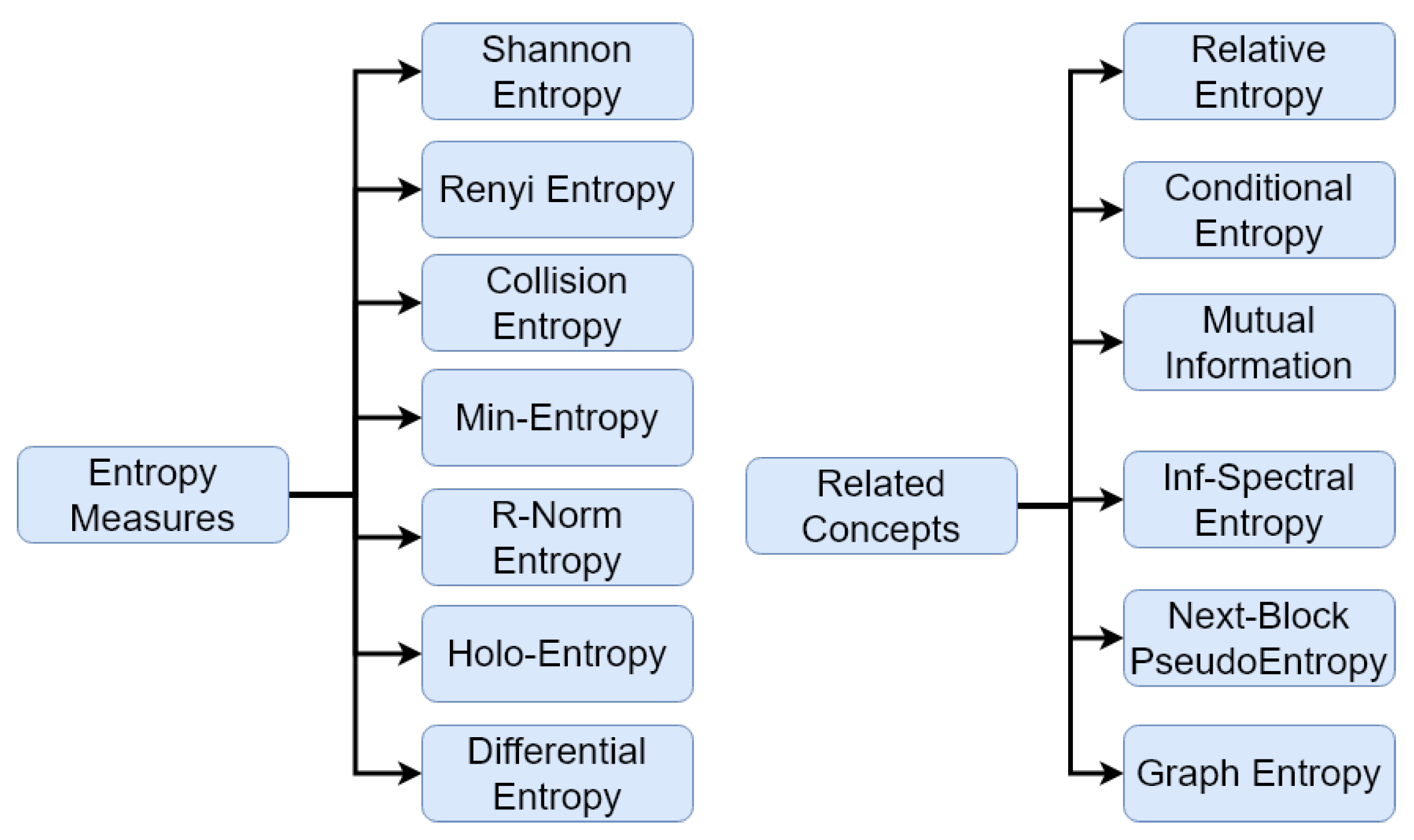
Entropy Free Full Text The Odyssey Of Entropy Cryptography Html

Lightweight Cryptographic Primitives Download Scientific Diagram

2 Taxonomy Of Cryptographic Primitives Download Scientific Diagram
Comments
Post a Comment